Credit Score Software Development without Access to Sensitive Data
Achieving online banking application user growth, scaling the platform by 250 times while establishing robust security protocols.

Executive Summary
Code Separation with Safe Multi-Environment Setup
Our Customer
SavvyMoney offers a Smarter Credit Score Solution for online and mobile banking platforms. The company provides comprehensive credit score analysis, monitoring, full credit report, and personalized offers — all in one dashboard.
With SavvyMoney credit score solutions consumers have convenient unlimited access to their credit score anytime and anywhere. Company’s main objectives are to empower customers’ control over financial health, to help understand how financial decisions might impact scores, and to provide users with the best savings options.
The Obstacles They Faced
SavvyMoney’s application works with sensitive data of real users, therefore, the company needed to ensure strict separation of the application’s codebase from its configurations.
How We Helped
Romexsoft’s dedicated development team investigated SavvyMondey’s requirements for sensitive data protection and enabled development without access to sensitive data.
We ensured that the same application with the same codebase could be launched in different environments: Staging, QA, and Production.
The Challenge
Securing Sensitive Data Access
SavvyMoney’s primary challenge was to ensure secure storage and limited access, only by the authorized personnel, to all passwords for database access, API tokens, and other sensitive configuration parameters for Production instances.
The Solution
Reliable Credit Score Software Deployment
SavvyMoney decided to choose AWS as their main hosting platform due to its scalability, reliability, constant innovations, low latency, and a huge variety of services. Romexsoft has successfully utilized a range of AWS tools during the development of the SavvyMoney’s app, ensuring the app’s high performance, global availability, and security.
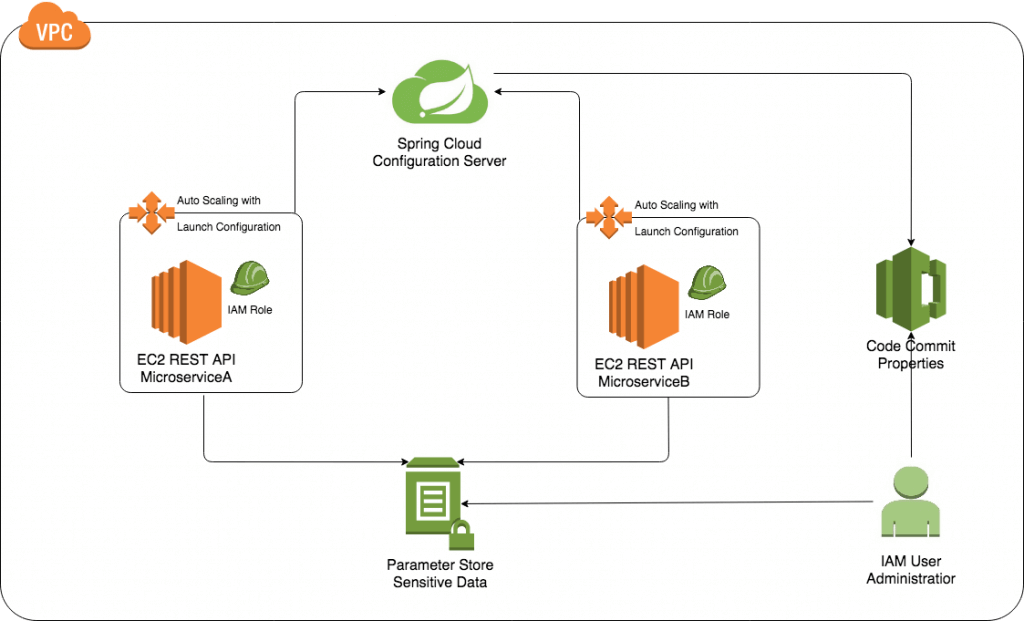
Romexsoft used AWS Systems Manager Parameter Store to provide secure and hierarchical storage for configuration data management and CodeCommit to make the collaboration on code easier.
SavvyMoney’s microservice architecture is built in Java Spring Boot framework. Each microservice is a separate REST API that performs the required business logic and is running on EC2 instances in the Autoscaling Group. Launch Configuration has an attached IAM role with read-only access to the parameter store. Therefore, any sensitive parameter is only known for the application on startup and there is no possibility to see it.
All sensitive configuration parameters from classic *.properties files are moved into the AWS Parameter Store and all *.property files with other parameters are moved into the CodeCommit. Spring Cloud Config service reads properties from CodeCommit, and REST API application calls Spring Cloud Config for required properties on startup or on-demand refresh. The access to Parameters store and CodeCommit have only the authorized employees.
Secure and Effective Development for Online Banking AWS Architecture Diagram
Verified by AWS
This case study is validated by AWS. Experts and professional auditors from AWS reviewed this case study and verified that we, Romexsoft, have built a functional infrastructure and efficient cloud solution.
It showcases the value that Romexsoft, being a certified AWS Advanced Tier Services Partner, delivers cloud solutions according to AWS standards and best practices.
The Results
Significant Users Growth and Stronger Data Security
Romexsoft helped SavvyMoney to scale up faster. The improvements we implemented enabled SavvyMoney to increase the number of users by 250 times and to keep it growing.
We ensured that the development team had no access to sensitive data either in Parameter Store or being logged on the EC2 instance. Our team made the separation of parameters storage on Parameter Store and Code Commit which provides better security, handling, and maintenance.
We enabled the possibility to reload parameters from Parameter Store without application rebuild and ensured rigid separation of the application’s codebase from its configurations.
Why Romexsoft
Builds Consistent Credit Scoring Software
Romexsoft is an AWS-certified Consulting Partner, trusted Software Development Company and Managed Service Provider, founded in 2004. We help customer-centric companies build, run, and optimize their cloud systems on AWS with creative, stable, and cost-efficient solutions.
Our key values
- Delivery of quality solutions
- Customer satisfaction
- Long-term partnership
We have successfully delivered 100+ projects and have a proven track record in FinTech, HealthCare, AdTech, and Media industries.
Romexsoft possesses a 5-star rating on Clutch due to its strong expertise, responsiveness, and commitment. 60% of our clients have been working with us for over 4 years.


