AWS: Overview of Security Processes Whitepaper
In this whitepaper we outlined the main security processes and features AWS offers its customers, namely:
- AWS Security Standards (Customer responsibility vs AWS responsibility)
- AWS Account Security Features
- AWS Service-Specific and Cloud Storage Security
- AWS Networking Services and Database Services Security
- AWS Security Best Practices & Essential AWS Security Documents
Security is a top priority for AWS, but one should always bear in mind that AWS Cloud Security is a shared responsibility between a customer and Amazon. This whitepaper will help you understand the zones of responsibility for each party.

Table of Contents
Table of Contents
AWS Cloud Security is a Shared Responsibility
Amazon Web Services (AWS) infrastructure, data centers and network architecture security standards are paramount and can hardly rival with on-premises setups most organizations have. The company employs the latest tech and talent to ensure utmost security and top service levels across 69 availability zones within 22 geographic Regions around the world. If there’s a new cybersecurity best practice in town, AWS is already using it. As well, the cloud services provider regularly executes penetration and the results are published within their compliance reports.
AWS Security Standards
There’s one important caveat it though: Amazon operates on the Shared Responsibility Model. This means that while they are doing their part of ensuring the security of the cloud, migration to the cloud does not relieve you of certain security responsibilities:
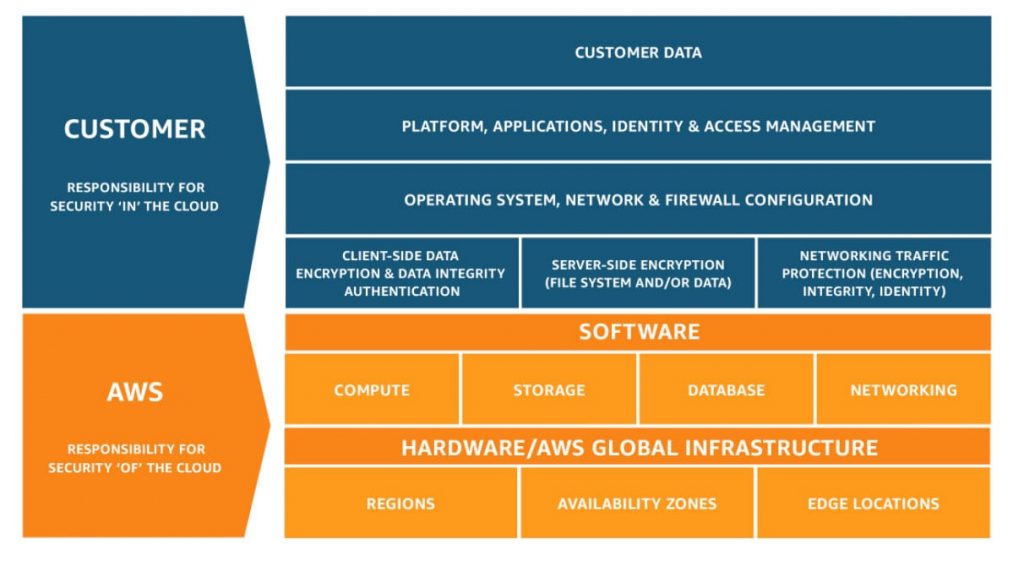
Source: Amazon
The amount of security configuration you must provide is virtually the same as you would provide in all of your systems and apps that would be housed within your own on-site infrastructure and networks. For example, when you issue passwords and key codes for access to your cloud-based infrastructure, it is your responsibility to keep those updated, change them regularly, and, of course, delete those accesses as employees leave or are no longer granted access. Failure to do so will put your organization at risk.
Indeed, the vast majority of Amazon cloud security breaches and data exposures did not occur due to technical hacking of the company’s systems. They were the result of the user’s negligence:
- In the most recent Capital One’s case, the bank misconfigured a cloud-based web application, thus creating a security loophole the hacker exploited.
- Last July, Attunity also misconfigured a server which resulted in a major customer data leakage, exposing data from companies like Netflix and Ford.
The good news, however, is that Amazon is very proactive in regards to providing its customers with the tools and technologies for protecting your assets. They are also offering a variety of support documentation, online training, workshops and even have a comprehensive Amazon cloud security certifications programs for IT staff. You can work through many of the managed services to perform your own security measures – but you must specifically perform them!
This AWS security processes whitepaper from Romexsoft provides you with a high-level overview of the main security features and processes Amazon has to offer you as a customer.
AWS Account Security Features
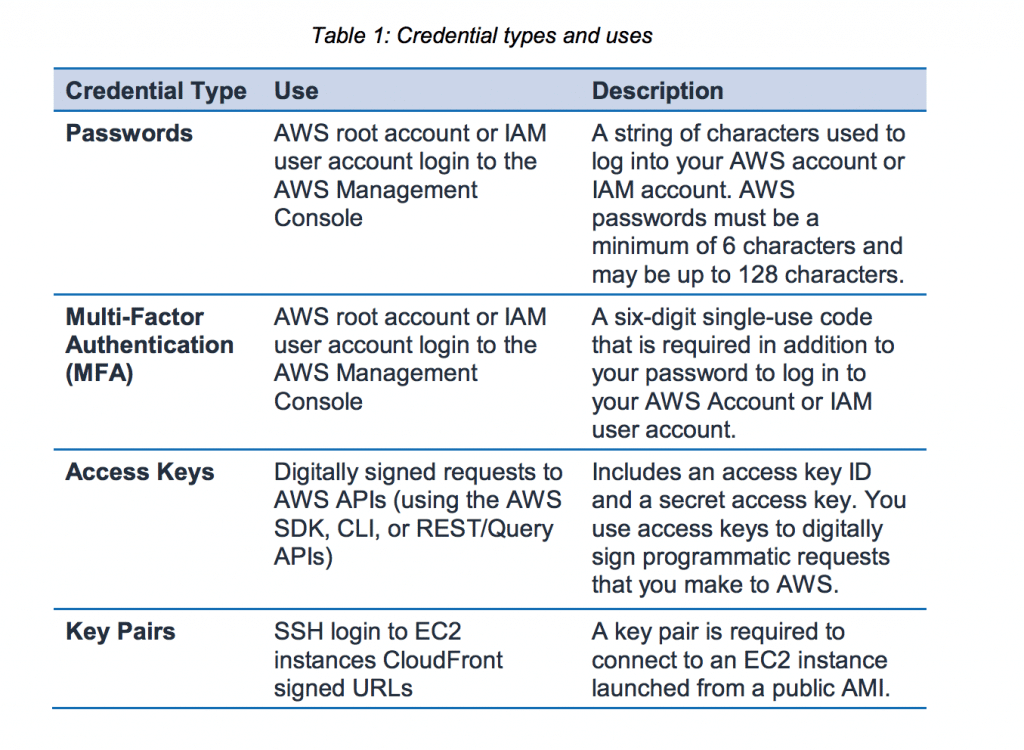
AWS uses a number of types of credentials for user authentication. No matter which ones you choose to use for each instance, you will always have access to a full Credential Report for your account.
AWS does recommend rotation of access keys and certificates on a regular schedule and gives you the support to do this without impacting performance or experiencing any downtime. So be sure to do that.
Other AWS account security mechanisms include:
- Secure HTTPS Access Points
- Security Logs
- AWS Trusted Advisor Security Checks
- AWS Config Security Checks
AWS Service-Specific Security
One of the underlying Amazon (AWS) security best practices for its product is multi-layer protection:
- First, they safeguard the infrastructure itself
- Next, they implement additional protection for individual Amazon services and make sure that they interact effectively and securely with all AWS networks and platforms.
You, as a customer, are then presented with an array of security mechanisms you should enable to protect your cloud setup. In this section, we’ll walk you through your options.
More read: List of Top 10 AWS cloud services
Amazon Elastic Compute Cloud (EC2), Amazon’s main Infrastructure as a Service (IaaS), comes with in-built protection on several levels:AWS Cloud Computing Security
- the operating system on the host platform
- Guest OS and virtual instances OS
- Firewall
- Signed API calls.
All of these measures together help prevent data interceptions. While Amazon does their part of securing EC2 on hardware level, you, as a customer, are expected to follow certain rules too:
- Access to Host OS is logged and audited. But it’s your job to ensure timely access revocation.
- Guest OS and virtual instances are under your full responsibility. As a customer, you will have full root access or admin control over those. Hence, ensure appropriate protection in regards to authentication, access management and so on.
- Amazon EC2 provides a complete firewall solution that can be configured to your needs.
- Use SSL-protected API endpoints.
Also, if you plan to use Amazon Elastic Block Storage, enable encryption of sensitive data with AES-256 (Amazon recommended).
AWS Networking Services Security
Most businesses rely on networking within their organizations and define, control and manage them internally. Moving networks to AWS does not change that. Any user can establish a private connection with AWS and control its networks access, just as has been done in-house.
Your job will be to define a private network connection to AWS, and establish the parameters, passwords, key codes, etc. that will allow access to each private network. You can create as many private networks as you wish, through AWS’s highly scalable DNS service and ensure that content is delivered to those with access.
Below are several key security practices for Amazon networking services.
Amazon Elastic Load Balancing: This service comes with several major security benefits:
- It will assume the encryption and decryption of Amazon EC2 instances with load balancing management.
- It will provide its users with one point of contact and support traffic encryption on networks that use HTTPS connections.
- Its TLS server certificate can be used to end client connections centrally, rather than having to be done on each instance.
Amazon Virtual Private Cloud (VPC): This service allows you to isolate a portion of your AWS cloud and deploy Amazon EC2 instances with private IP addresses there. Doing so will help you enable different levels of public access.
AWS Direct Connect Security: Through this feature, you can establish a direct link between your internal network and any AWS region. Not only will this reduce your user costs, but you can also then set up virtual interfaces that will bypass any internet service provider. This takes out an intermediate step that can expose your data.
With Direct Connect, you can set up direct virtual interfaces, and obtain rack space within the location nearest to you geographically as well as connect to other desired regions. Your dedicated connection can be partitioned into several virtual interfaces, letting you use the same connection to access all of your EC2 instances as well as objects that you have stored in AWS S3. And, you can maintain separation between your public and private environments.
You can find more useful information via a link: AWS HIPAA Compliance: Best Practices Checklist
Amazon Cloud Storage Security
Amazon Simple Storage Service (Amazon S3): The first key step of Amazon cloud drive security is creating appropriate Identity and Access Management procedures, along with Access Control Lists (ACL’s), which will allow and/or terminate/deny access within a single AWS S3 storage bucket. As a customer, you can choose to use your own encryption or one that is provided by AWS.
Additionally, stick with the next best practices:
- Transfer data from S3 only using SSL-encrypted endpoints.
- Create customized bucket security policies for different types of assets.
- Log access to buckets and objects within them.
Amazon S3 Glacier Security is the optimal durable storage for data that are not accessed. The data is automatically encrypted, and only a client’s specific account can access it. A client can also use AWS IAM to control access by users to any given bucket or vault.
AWS Import/Export Security: When it is necessary to migrate large chunks of data to S3, EBS, or S3 Glacier, organizations need a rapid and secure method for doing so. Here is a chart showing how AWS encrypts these jobs:
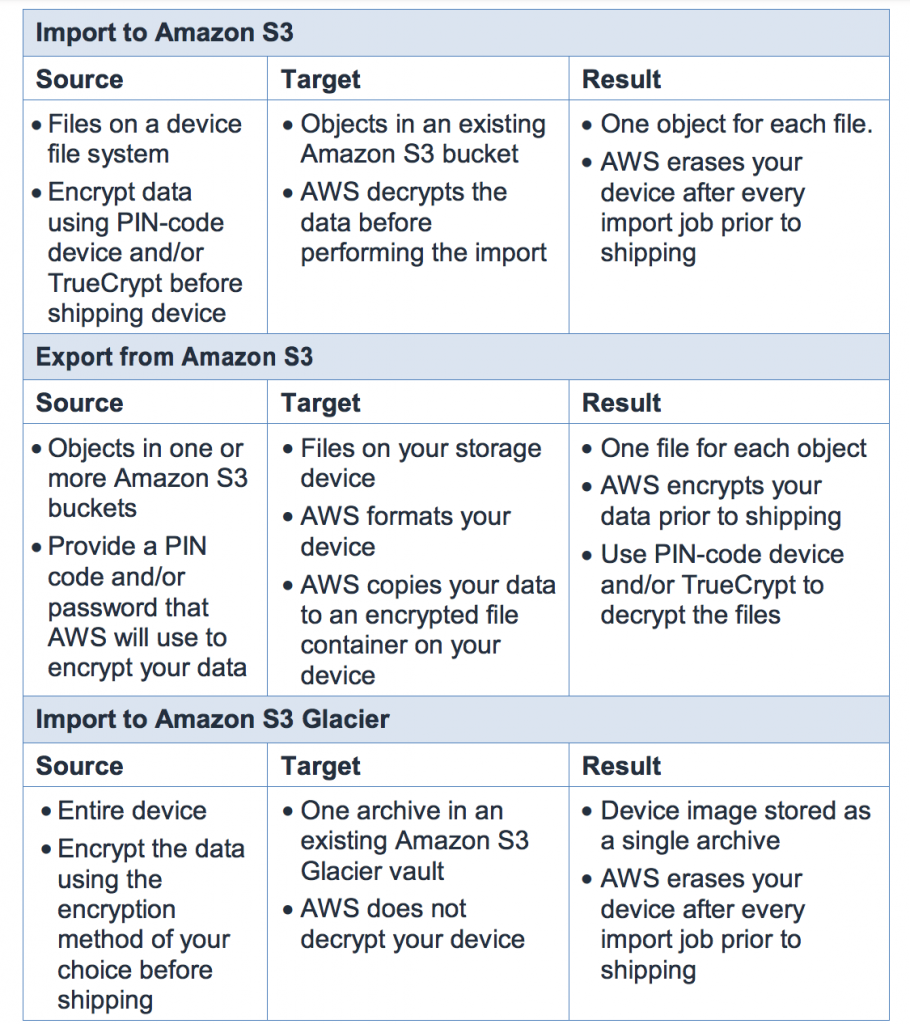
Database Services
Amazon DynamoDB Security: Distributed databases can be offloaded to AWS without concern for all of those pesky things like hardware provision, patching, cluster scaling, set up or configuration. It is also possible to set up automatic backups of your databases. You can separate out parts of databases via regions, and obviously, such copies provide disaster recovery (DR) should the original database be corrupted by any user.
Additionally, you are provided with the following security mechanisms:
- You can control access to parts or the entire database as well, by setting up respective IAM permissions.
- If needed, you can also opt for web identity federation to control access from users authenticated via by Login with Amazon, Facebook, or Google.
Amazon Relational Database Service (RDS) Security: Amazon RDS enables you to set up relational database instances and to scale and store them as needed, for rapid retrieval. Again, you are in control of access by setting up DB Security Groups. The default mode is “deny all” access and then you must specifically provide for individual access to all or parts of your DB. And, if you want more control, you can operate your DB instances in a VPC.
AWS also has Automatic Software Patching to make sure the database software is up-to-date. You are notified when patches are needed and you can apply them through the AWS maintenance window.
You will also receive notifications of several things – when maintenance has been scheduled if the instance was shut down and why, when a backup has been initiated when your security group has been altered, and even when your storage space is running low.
Read more about AWS Backup and Disaster Recovery
Managed AWS Services
You have a wealth of AWS managed services that can be used with your applications, including streaming, queueing, search, push notifications, and email deliveries such as:
- Amazon CloudSearch: set up a search feature on your website, without you having to do anything. Again, you control who has access to these functions. And as the volume of searches goes up and down, AWS automatically fluctuates to meet those needs.
- Amazon Simple Queue is a messaging service. It provides a communication queuing service between and among distributed application components. AWS SQS access is only granted based on client account or IAM policies of the client. It is important to note that AWS does not encrypt data. A user must encrypt that data before it is migrated and must ensure that decryption methods are also embedded. Encrypting messages before they go to AWS will protect access by unauthorized people.
- Amazon Simple Notification Service (SNS) Security: If you are looking for a way to send secure notifications seamlessly, at low cost, and to publish messages from any of your applications to your subscribers, then you are looking for AWS SNS. Administrators of an application can control the topics, the messages, control who sends and receives them and secure them against any unauthorized access.
- AWS AppStream service is a framework for allowing streaming applications to any customer device. Again, access to this framework must be authorized before getting a session ID. Identifies of users of this service must be authenticated, and AWS provides this. You want to be certain that anyone connecting to and using your applications is authorized.
Two More Service-Neutral AWS Security Best Practices
DDoS Protection and Prevention: A Distributed Denial of Service (DDoS) attack is a deliberate attempt to make a migrated system unavailable to authorized users. Such attackers can use a variety of techniques, but all will disrupt access for legitimate users.
AWS provides both infrastructure and services that will help its customers mitigate DDoS:
- Amazon Route 53
- Elastic Load Balancing
- Amazon CloudFront
- Amazon Wifewall to control traffic and to deflect unauthorized requests
AWS provides sufficient information that explains typical DDoS attacks the strategies for protection. Clients must review these best practices so that they can take a lead and important role in prevention.
Security Groups: This is a fundamental Amazon security best practice. Security groups behave like a firewall to control the traffic that is allowed into your EC2 instances. They can be both region and VPC specific. When a client sets up a security group in one region or VPC, it can only be used there. So, when a new EC2 is launched, a security group must be specified. Once an instance is launched, however, new security groups can be added, deleted or modified by a client, and the rules of access will apply to all of those security groups.
More read: The Top 5 Application Migration Best Practices
Further Reading: The Essential AWS Security Documents
- AWS Security Best Practices – This guide provides security best practices that will help you define your Information Security Management System (ISMS) and build a set of security policies and processes for your organization so that you can protect your data and assets in the AWS Cloud.
- AWS: Overview of Security Processes – This whitepaper describes the physical and operational security processes for the AWS managed network and infrastructure, and helps answer questions such as, “How does AWS help me protect my data?”
- Architecting for HIPAA Security and Compliance on AWS – This whitepaper describes how to leverage AWS to develop applications that meet HIPAA and HITECH compliance requirements.
- Service Organization Controls (SOC) 3 Report – This publicly available report describes internal AWS security controls, availability, processing integrity, confidentiality, and privacy.
- Introduction to AWS Security –This document provides an introduction to AWS’s approach to security, including the controls in the AWS environment, and some of the products and features that AWS makes available to customers to meet your security objectives.
- AWS Best Practices for DDoS Resiliency – This whitepaper covers techniques to mitigate distributed denial of service (DDoS) attacks.
- AWS: Risk and Compliance – This whitepaper provides information to help customers integrate AWS into their existing control framework, including a basic approach for evaluating AWS controls and a description of AWS certifications, programs, reports, and third-party attestations.
- Use AWS WAF to Mitigate OWASP’s Top 10 Web Application Vulnerabilities – AWS WAF is a web application firewall that helps you protect your websites and web applications against various attack vectors at the HTTP protocol level. This whitepaper outlines how you can use AWS WAF to mitigate the application vulnerabilities that are defined in the Open Web Application Security Project (OWASP) Top 10 list of the most common categories of application security flaws.
- Introduction to Auditing the Use of AWS – This whitepaper provides information, tools, and approaches for auditors to use when auditing the security of the AWS managed network and infrastructure.
- AWS Security and Compliance: Quick Reference Guide – By using AWS, you inherit the many security controls that we operate, thus reducing the number of security controls that you need to maintain. Your own compliance and certification programs are strengthened while at the same time lowering your cost to maintain and run your specific security assurance requirements. Learn more in this quick reference guide.
Final Word
Security must be top of mind for every organization who plans to migrate to AWS. Amazon is a highly-secure cloud environment, but only when you place the necessary controls in place. As this paper illustrates, there are a lot of facets to account for. If you lack the expertise in the matter, reach out to Romexsoft team – a certified AWS partner company, offering end-to-end cloud services. Get in touch with us!



