Security and Privacy Solutions in EHR Development
One data breach costs $3.7 million in lost revenues. Learn about the essential EHR features to patch all the vulnerabilities and keep patient data safe.

Healthcare data breaches cost hospitals over $3.6 billion in 2017 and almost 90% of hospitals have reported a data breach in the past two years according to the latest IBM Security report. Their team has also estimated that 27.7% of the organizations surveyed for the report can experience a material data breach within the next 24 months.
These staggering numbers can be largely attributed to the fact that most healthcare providers still use outdated legacy systems – think 10+ years old software that has never been updated by developers to resist modern cyber threats.
For many healthcare providers planning to undertake an EMR/EHR development project, system security still remains an afterthought. After all, those budgets could be spent elsewhere, right?
But think about the breach numbers again.
Single breach results in a $3.7 million loss in direct revenues for the provider and over $500,000 loss in brand value, not to mention the fines imposed by the Health Insurance Portability and Accountability Act (HIPAA). Obviously, implementing comprehensive EHR security solutions early on will cost you less.
This post outlines the current EHR/EMR security vulnerabilities and the respective tech best practices to implement.
The Main EHR Security Threats To Account For
In 2016, data breaches in healthcare have doubled reaching a whopping one data breach per day and affecting over 27 million patient records in the US alone.
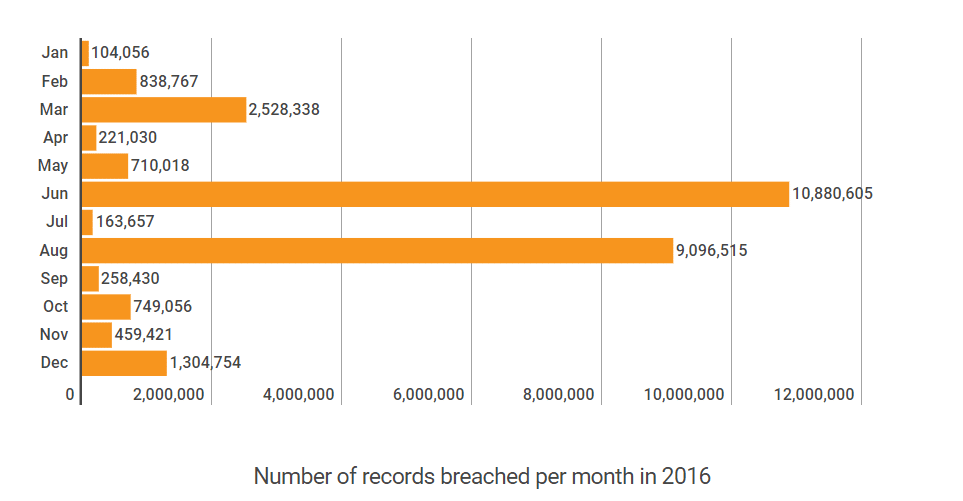
Source: Protenus, Inc. & DataBreaches.net
In most cases, however, these breaches can be attributed to a handful of vulnerabilities that could be easily “patched”. According to the same IBM study, most of the breaches occur due to either of the next reasons:
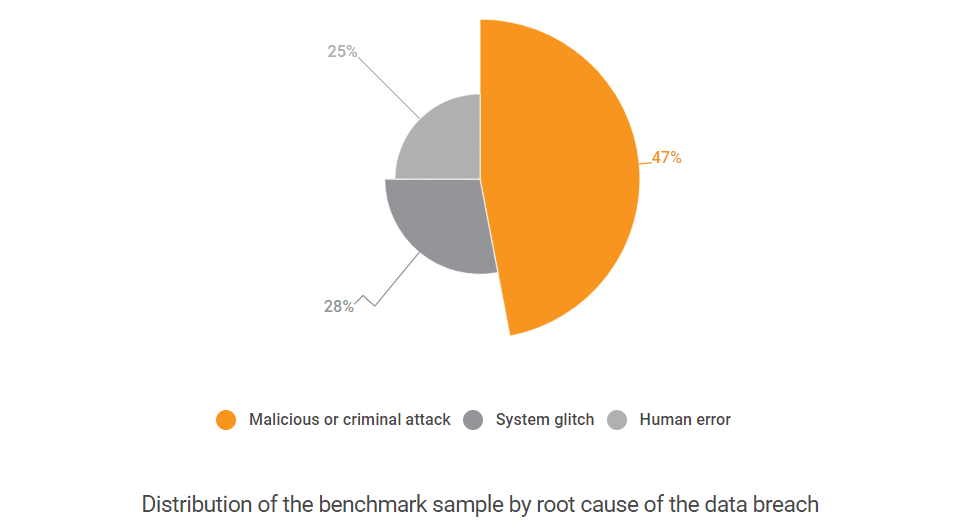
The National Academies of Sciences, Engineering, and Medicine offers a more detailed categorization of all the electronic health records security and privacy concerns:
Threat 1: Insiders who make a “mistake” that leads to accidental disclosures. Arguably, this is the most common reason for breached privacy as it can occur in a million of ways – misaddressed emails, misclassified data, sensitive data visible on the computer screen and so on.
Threat 2: Insiders abusing the granted access privileges. A common example is one curious lab technician, who violates the trusts associated with their access permission and browses all available data out of mere curiosity. For instance, to inquire about a friend’s or co-worker’s well-being or get some health care data about the admitted celebrity patients such as local politicians, athletes and so on.
Threat 3: Insiders who access the information for profit or for spite. An attacker has a certain level of authorization to the system, but decided to hamper the system further and receives unauthorized access to additional data. For instance, that could be someone from a billing department gaining access to the patient’s full medical history and disclosing all the information to a 3rd party. Stolen EHR charts were reported to be sold for $50 a pop on the black market. Selling some celebrity healthcare data to some yellow press can net the criminals a much larger sum though.
Threat 4: Unauthorized physical intrusion. The intruder in this case, merely walks in the hospital in a lab coat and with a fake badge and gains physical access to a workstation or asks other employees to disclose health information.
Threat 5: Former/current employees and outsiders, who plan attacks to gain access to health information, damage the system, and disrupt operations. This is a purely technical threat to the EHR systems. Particularly, they are targeting the records available via an external network and stored in the cloud.
So why cyber-criminals are after the patient data? According to Don Jackson, director of threat intelligence at PhishLabs, stolen health records can go for $10 each, which is 10 to 20 times the value of a U.S. credit card number. These records are later used to create fake IDs for buying prescription-only medicine and/or medical equipment and re-sell it on the black market. Other use cases include filling up fake insurance claims and receiving compensation or fraudulently bill hospitals. As a result, it’s crucial to spot Fake IDs to prevent such fraudulent activities and protect both individuals and institutions from significant financial losses.
Additionally, this threat level includes the so-called “denial of service” attacks. These can include distributing system viruses that will encrypt or delete critical data files. In 2016, 72% of all malware attacks on medical institutions were ransomware – a nasty virus extorting payment for accessing your data.
In fact, EHR privacy and security issues cost hospitals a lot. The average cost of a healthcare data breach is $225 per record. Additionally, after a ransomware attack, healthcare institutions are obliged to call in auditors to determine the scale of compromised information. The audit can hamper the operations for months and cost the hospital $610,000 and upward.
Next, it’s also important to account for the time required to identify and contain the breach. The average time to identify the breach was 191 days, and it took an additional 66 days to contain it for most hospitals as IBM indicates. Such a prolonged timeline is largely attributed to the considerable complexity of the IT security architecture. The modern providers now need to account for the cloud-based applications, mobile apps security, and BYOD policies. Hence, you will need to clearly define the required set of custom EHR security features worth implementing in the first place.
Security Solutions in EHR Development
HIPAA/HITECH Compliance: Being compliant isn’t optional, especially when it comes to the official standards for privacy and security. Previously, we have shared an extensive HIPAA Compliance Requirements Checklist that lists all the provisions you should follow during an EMR software development project. It enlists the key security standards to adhere to.
Additionally, you can use the official HIPAA Security List Assessment Tool to understand what your system is lacking right now.
Secure Document Exchange: E-documents flow in all directions – within your institution; between different providers; between the provider and governmental registries. Protecting these exchanges is critical to avoid breaches. Use data encryption for all the communication and advanced virus scanning to filter potentially hazardous messages. The rule of thumb here is to use the encryption standards proposed by the National Institute of Standards and Technology.
It is also mandatory to encrypt messages for patients, who want to receive an electronic copy of their records. A secure patient’s password or keyword can be given to them in person during their visit. Speaking of passwords…
More read: AWS: Overview of Security Processes Whitepaper.
Advanced Password Protection: All the users must be asked to create secure passwords, and those must be changed every 60-90 days. You can also enable two-factor authentication after the password change for added protection. The same measures could be implemented for the patient portal too. Sure this may initially cause some disadvantages and complaints from the staff, but a weak password is the fastest getaway to stealing patient data.
Roles-Based Access Control: The basic required minimum is to have the next procedures in place:
- Unique user identification.
- Emergency access procedures.
- Automatic logoff.
- Encryption and decryption.
Next, you will need to develop an RBAC matrix that will outline the initial access rights from different groups of users. It will then enable the security team to detect who can perform certain tasks; when; from what area and in what order. Any unusual movements can be automatically detected and reported to the administrators.
From the tech standpoint, implementing RBAC assumes the next framework:
- Creating security labels to represent the privacy of a data object and create a respective policy inside the database.
- The database architects should work on creating a proper hierarchy to correctly maintain role memberships for the operations of the system.
- Next, they will need to define what view will be used to display the data and implement the prevention mechanisms for accessing the base table (all data records) by random users.
- Afterward, mechanisms controlling the visibility of the data based on user permissions should be created. Most modern databases allow partial data encryption that will ensure that.
Audit Trail System: This part of the software will be essential to locate the possible breach due to unauthorized access. It is designed to track all user actions within the system and report whenever any unusual activity is detected.
Specifically, it should help you answer the next questions:
- What data was accessed?
- When did it happen?
- Who accessed it?
- Where was it accessed from?
Predictive Analytics for Fraud Detection. An AI-powered solution can help you detect “rule-breaking” behaviors within your system and detect abnormal usage patterns such as suspicious payments or data transmission to unknown recipients. A robust predictive analytics system will not only flag potentially fraudulent activities but also give the reasoning for that and learn over time to mark new threads and patterns. Get more insights on the matter from our previous post.
Data Leakage Prevention Tools can help you avoid the breach spreading outside the facility. The available software integrations for that are plentiful, however, before implementing a certain tool, do the following:
- Conduct a thorough audit first. If you are not sure where the critical data is stored; what data security regulations are already met or not, then implementing a DLP tool will not bring much value to your institution.
- Treat it as a long–term program. The cost to develop an EMR system with an integrated DLP tool will not be exorbitant. However, a lot of internal resources will be required once the new tool is in place. All the accumulated data will need to be located, classified and categorized based on the different factors on an ongoing basis. You may want to enlist the help of some data scientists for that.
These were the essential security features that could be implemented for your EHR solution. The ultimate list, however, will largely depend on your operational framework and the current solutions in place.
Romexsoft team would be delighted to provide further consultations on medical software development or AWS cloud security and outline exactly how you can protect your institution from costly data breaches.





